VMASC Year-In-Review FY 2023 Publications and Projects
As Virginia's premier university research center, the Old Dominion University (ODU) Virginia Modeling Analysis, and Simulation Center (VMASC) focuses on applied research leading to digital transformation. This Year-in-Review offers a retrospective glimpse into the 2023 Fiscal Year, highlighting a selection of the publications and projects our team members have been involved with over the year.
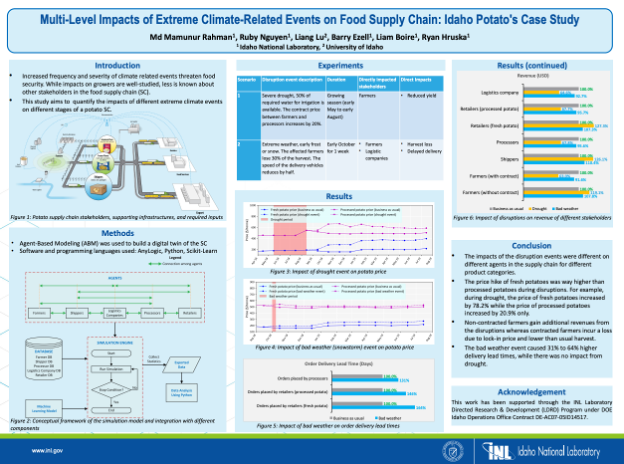
Multi-Level Impacts of Extreme Climate-Related Events on Food Supply Chain: Idaho Potato's Case Study
Authors: Liang Rahman, Md Mamunur, Nguyen, Ruby Thuy, Ezell, Barry, Charles, Boire, Liam D, and Hruska, Ryan C (2022)
Increased frequency and severity of climate related events threaten food security. While impacts on growers are well-studied, less is known about other stakeholders in the food supply chain (SC). This study aims to quantify the impacts of different extreme climate events on different stages of a potato SC. Agent-Based Modeling (ABM) was used to build a digital twin of the SC. Two experiments were conducted: (1) Severe drought, 50% of required water for irrigation is available. The contract price between farmers and processors increases by 20%. (2) Extreme weather, early frost or snow. The affected farmers lose 30% of the harvest. The speed of the delivery vehicles reduces by half. Results: The impacts of the disruption events were different on different agents in the supply chain for different product categories. The price hike of fresh potatoes was way higher than processed potatoes during disruptions. Non-contracted farmers gain additional revenues from the disruptions whereas contracted farmers incur a loss due to lock-in price and lower than usual harvest. The bad weather event caused 31% to 64% higher delivery lead times, while there was no impact from drought.
Reprioritizing Emergency Management Resources for Pandemic and Other Hazards
Authors: Ronnie E. Hill Jr., Davis C. Loose, DeAndre Johnson, Stacy McKinley, Wie Yusuf, Leigh M. Chapman, Thomas L. Polmateer, Barry C. Ezell, and James H. Lambert (2023) Hazard mitigation planning, whether on a global, national, regional, or local level requires a multitude of organizations to collaborate on scenarios of mutual concern. Agencies strategize, develop, and implement plans for mitigating effects from manufactured and natural disasters. To develop more effective mitigation strategies, a typical agency uses a hazard gap analysis to identify gaps and evaluate the maturity of mitigation action strategies across jurisdictions. Issues of shared governance and competing perspectives create challenges for managing disasters across multiple tiers of government. This paper contributes a method to identify the agency perspectives on disaster risk that most matter to the allocations and priorities for shared resources. Each agency perspective is represented as a scenario of one or more emergent and future conditions. The conditions include health, environment, technologies, wear and tear, workforce, information, communication, obsolescence, regulation etc. In quantifying the disruption of system order, the paper presents an example of a risk register with 40 capabilities, six ordering criteria and eight scenarios. The new method coordinates data, evidence, experience, and imagination that are essential to systems analysis and negotiation of requirements among emergency managers in the post-pandemic era.
Published in the ASCE Journal for Natural Hazard.
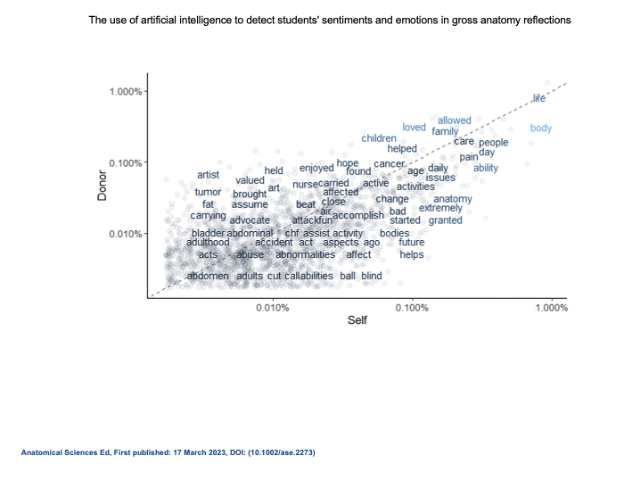
The use of artificial intelligence to detect students' sentiments and emotions in gross anatomy reflections.
Authors: Rechowicz, K. J. & Elzie, C. A. (2023). Students' reflective writings in gross anatomy provide a rich source of complex emotions experienced by learners. However, qualitative approaches to evaluating student writings are resource heavy and timely. To overcome this, natural language processing, a nascent field of artificial intelligence that uses computational techniques for the analysis and synthesis of text, was used to compare health professional students' reflections on the importance of various regions of the body to their own lives and those of the anatomical donor dissected. A total of 1365 anonymous writings (677 about a donor, 688 about self) were collected from 132 students. Binary and trinary sentiment analysis was performed, as well as emotion detection using the National Research Council Emotion Lexicon which classified text into eight emotions: anger, fear, sadness, disgust, surprise, anticipation, trust, and joy.
The most commonly written about body regions were the hands, heart, and brain. The reflections had an overwhelming positive sentiment with major contributing words “love” and “loved.” Predominant words such as “pain” contributed to the negative sentiments and reflected various ailments experienced by students and revealed through dissections of the donors. The top three emotions were trust, joy, and anticipation. Each body region evoked a unique combination of emotions. Similarities between student self-reflections and reflections about their donor were evident, suggesting a shared view of humanization and person-centeredness. Given the pervasiveness of reflections in anatomy, adopting a natural language processing approach to analysis could provide a rich source of new information related to students' previously undiscovered experiences and competencies.
From Cyclones to Cybersecurity: A Call for Convergence in Risk and Crisis Communications Research, PNAS Nexus (Submitted July 2023)
Authors: Ann Marie Reinhold, Ross J. Gore, Barry C. Ezell, Clemente Izurieta, and Elizabeth A.Shanahan, (2023) A robust body of literature investigates mechanisms for improving risk communication because effective risk communication saves lives. While effective risk communication strategies are equally desired across different hazard domains (e.g., natural hazards, cyber security), the extent to which risk communication experts utilize the “lessons learned” from disciplines outside their own is suspect. Therefore, we hypothesized that risk communication research is siloed according to scientific disciplines at the detriment to the advancement of the field of risk communications research writ large. We test this hypothesis by evaluating the disciplinarity of 5,264 published papers using a combination of simple descriptive statistics, natural language processing, and hierarchical clustering. Finding that the risk communication research is siloed according to disciplinary lexicons, we present our findings as a call for convergence amongst our risk and crisis communication scholars to bridge across our disciplinary silos. In so doing, we will increase our ability to affect transformative change in the efficacy of our risk and crises messages.


Opportunities and Challenges of Using Computer-Based Simulation in Migration and Displacement Research: A Focus on Lesbos, Greece.
Authors: Frydenlund, E., and Padilla, J. (2022).
While simulation models have been used in the study of human migration, it is not broadly accepted as a research method. The chapter introduces the benefits and shortcomings of using simulation models to study migration and displacement.
Did They Really Tweet That? Querying Fact-Checking Sites and Politwoops to Determine Tweet Misattribution
Authors: C Bradford, ML Nelson (2022).
Screenshots of social media posts have become common place on social media sites. While screenshots definitely serve a purpose, their ubiquity enables the spread of fabricated screenshots of posts that were never actually made, thereby proliferating misattribution disinformation. With the motivation of detecting this type of disinformation, we researched developing methods of querying the Web for evidence of a tweet's existence. We developed software that automatically makes search queries utilizing the body of alleged tweets to a variety of services in an effort to find fact-check articles and other evidence of supposedly made tweets. We also developed tools to automatically search the site Politwoops for a particular tweet that may have been made and deleted by an elected official. In addition, we developed software to scrape fact-check articles from the sites Reuters.com and Snopes.com in order to derive a “truth rating" from any given article from these sites.
Robots still outnumber humans in web archives, but less than before
Authors: HR Jayanetti, K Garg, S Alam, ML Nelson, MC Weigle (2022).
To identify robots and humans and analyze their respective access patterns, we used the Internet Archive’s (IA) Wayback Machine access logs from 2012 and 2019, as well as Arquivo.pt’s (Portuguese Web Archive) access logs from 2019. We identified user sessions in the access logs and classified those sessions as human or robot based on their browsing behavior. To better understand how users navigate through the web archives, we evaluated these sessions to discover user access patterns. Based on the two archives and between the two years of IA access logs (2012 vs. 2019), we present a comparison of detected robots vs. humans and their user access patterns and temporal preferences. The total number of robots detected in IA 2012 is greater than in IA 2019 (21% more in requests and 18% more in sessions). Robots account for 98% of requests (97% of sessions) in Arquivo.pt (2019).
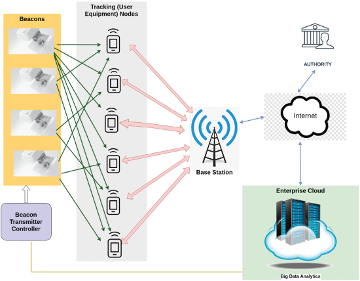
Securing Age-of-Information (AoI)-Enabled 5G Smart Warehouse Using Access Control Scheme
Authors: A. K. Das, S. Roy, E. Bandara and S. Shetty (2023).
Warehouses are becoming more dependent on connected technologies to support the tracking of items to the automated systems that may control these items (move to proper locations) or even support a manufacturing process. Wi-Fi is good but tends to struggle in large areas. We could overexpose a warehouse with many Wi-Fi access points, but this would increase the time to communicate (imagine a message having to jump to each access point to get from one end of the warehouse to the other). Instead, researchers are investigating the use of 5G wireless technology like what you would use on your smartphone but privately run just for the warehouse. In this type of system, the communication could occur faster as it would not have to jump through each access point due to the ability to manipulate the RF signal with powerful radios that can be dynamically reconfigured based on the needs and changing state of the warehouse.
To support this research endeavor, the researchers at CSICS/VMASC are contributing to ensure that the new system can operate fast, efficiently and most importantly secure! Many of the 5G sensors are very small with limited resources resulting in a low power requirement. New protocols are needed to maintain great security without the requirement of unlimited power and without compromising the benefits 5G brings to the speed of communication. In the paper titled "Securing Age-of-Information (AoI)-Enabled 5G Smart Warehouse Using Access Control Scheme", published in IEEE Internet of Things Journal this year, aims to design an energy-efficient certificate-based access control protocol, that will ensure the real-time and secure message communication among various participating agents of the smart warehouse. The authors describe the protocol encouraging other researchers to utilize and build on it, while additionally presenting performance results of test systems using the proposed protocol.
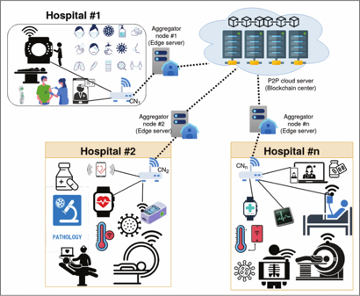
Quantum Resistance Cryptographic Methods to Improve Security in Health Medical Devices
Authors: P. Bagchi, B. Bera, A. K. Das, S. Shetty, P. Vijayakumar and M. Karuppiah
Cryptography, in particular public private key (PKI) cryptography is used to secure our communications over public networks. The security of PKI is measured by the time it would take classical computers to try different calculation of prime factors and identify the Key to decrypt the message data. Classical computers being binary in nature take a long time to do this type of calculation when the factors are very large which is the standard for PKI methods. Quantum computers (which are only implemented on a very small scale and performance today) are not binary in nature and allow for them to compute many more states at the same time compared to classical computers. Because of this, quantum computing could very easily identify the key to decode current cryptography best practices. Although it appears we are likely a couple of decades before quantum computers can crack current standards, researchers are currently planning and developing new cryptographic algorithms that can be “quantum resistant” where even if quantum computers would not be able to easily find the key in order to decrypt messages.
To support the research endeavor VMASC is partnering with International Institute of Information Technology, India to better utilize these new algorithms within known high level secure use cases. One of these use cases is in regard to personal private information related to medical healthcare devices. The team published the paper “Post Quantum Lattice-Based Secure Framework using Aggregate Signature for Ambient Intelligence Assisted Blockchain-Based IoT Applications” in IEEE Internet of Things Magazine this past March 2023. The paper describes how prior defined Lattice-Based public private key algorithms which would be hard for quantum computers to crack could be implemented within Internet of Things medical devices. The exchange of public keys and signatures were demonstrated using private blockchains with the idea of adding trust and transparency to the storage and update of key information. This algorithm ultimately provides an avenue for system implementors when quantum computers become more of a reality and is another instance of security researchers getting ahead of the attackers even when the attackers require new technology that is still being developed.
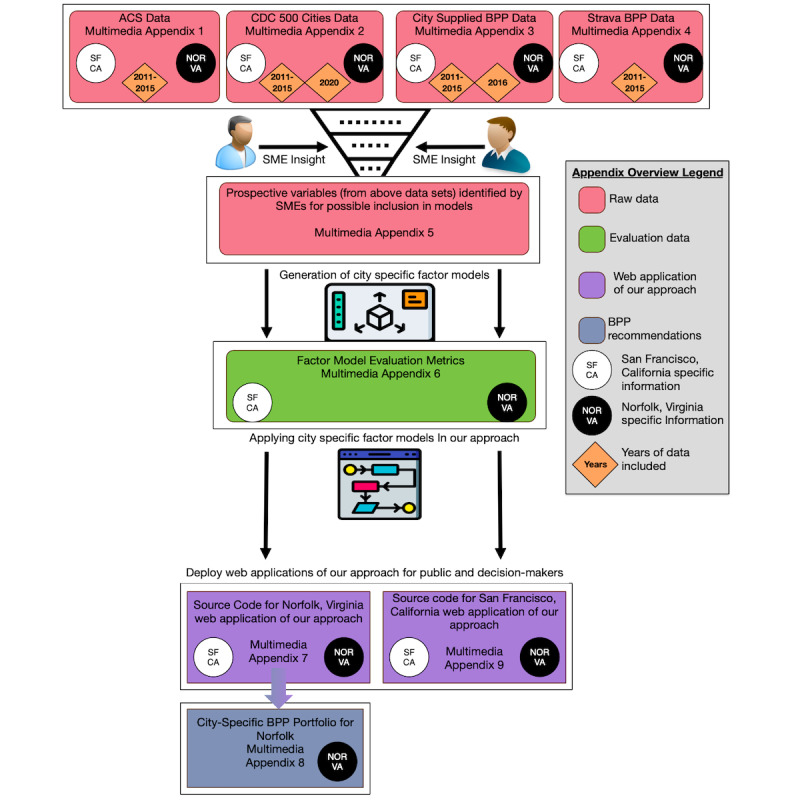
Estimating the health effects of adding bicycle and pedestrian paths at the census tract level: multiple model comparison
Authors: R. Gore, C. J. Lynch, C. A. Jordan, A. Collins, R. M. Robinson, G. Fuller, P. Ames, P. Keerthi, and Y. Kandukuri (2022)
Adding additional bicycle and pedestrian paths to an area can lead to improved health outcomes for residents over time. However, quantitatively determining which areas benefit more from bicycle and pedestrian paths, how many miles of bicycle and pedestrian paths are needed, and the health outcomes that may be most improved remain open questions. Our work provides and evaluates a methodology that offers actionable insight for city-level planners, public health officials, and decision makers tasked with the question “To what extent will adding specified bicycle and pedestrian path mileage to a census tract improve residents’ health outcomes over time?” We conducted a factor analysis of data from the American Community Survey, Center for Disease Control 500 Cities project, Strava, and bicycle and pedestrian path location and use data from two different cities (Norfolk, Virginia, and San Francisco, California).
We constructed 2 city-specific factor models and used an algorithm to predict the expected mean improvement that a specified number of bicycle and pedestrian path miles contributes to the identified health outcomes. We show that given a factor model constructed from data from 2011 to 2015, the number of additional bicycle and pedestrian path miles in 2016, and a specific census tract, our models forecast health outcome improvements in 2020 more accurately than 2 alternative approaches for both Norfolk, Virginia, and San Francisco, California. Furthermore, for each city, we show that the additional accuracy is a statistically significant improvement (P<.001 in every case) when compared with the alternate approaches. For Norfolk, Virginia (n=31 census tracts), our approach estimated, on average, the percentage of individuals with high blood pressure in the census tract within 1.49% (SD 0.85%), the percentage of individuals with diabetes in the census tract within 1.63% (SD 0.59%), and the percentage of individuals who had >2 weeks of poor physical health days in the census tract within 1.83% (SD 0.57%). For San Francisco (n=49 census tracts), our approach estimates, on average, that the percentage of individuals who had a stroke in the census tract is within 1.81% (SD 0.52%), and the percentage of individuals with diabetes in the census tract is within 1.26% (SD 0.91%).
Classifying Mathematics Teacher Questions to Support Mathematical Discourse.
Authors: Datta, Debaiyoti, Bywater, James P., Phillips, Maria, Lilly, Sarah, Chiu, Jennifer L., Watson, Ginger S., & Brown, Don E.
This paper examines whether natural language processing technologies can provide teachers with high-quality formative feedback about questioning practices that promote rich inclusive mathematical discourse within classrooms. This paper describes how a training dataset was collected and labeled using teacher questioning classifications that are grounded in the mathematics education literature, and it compares the performance of four classifier models fine-tuned using that dataset. Of the models tested, we find that RoBERTa, an open-source LLM, had a 76% accuracy in classifying questions. These modern transfer-learning based approaches require significantly fewer data points than traditional machine-learning methods and are ideal in low-resource scenarios like question classification. The paper concludes by discussing potential use cases within the field of mathematics teacher education and describes how the classifier models created can be publicly accessed.
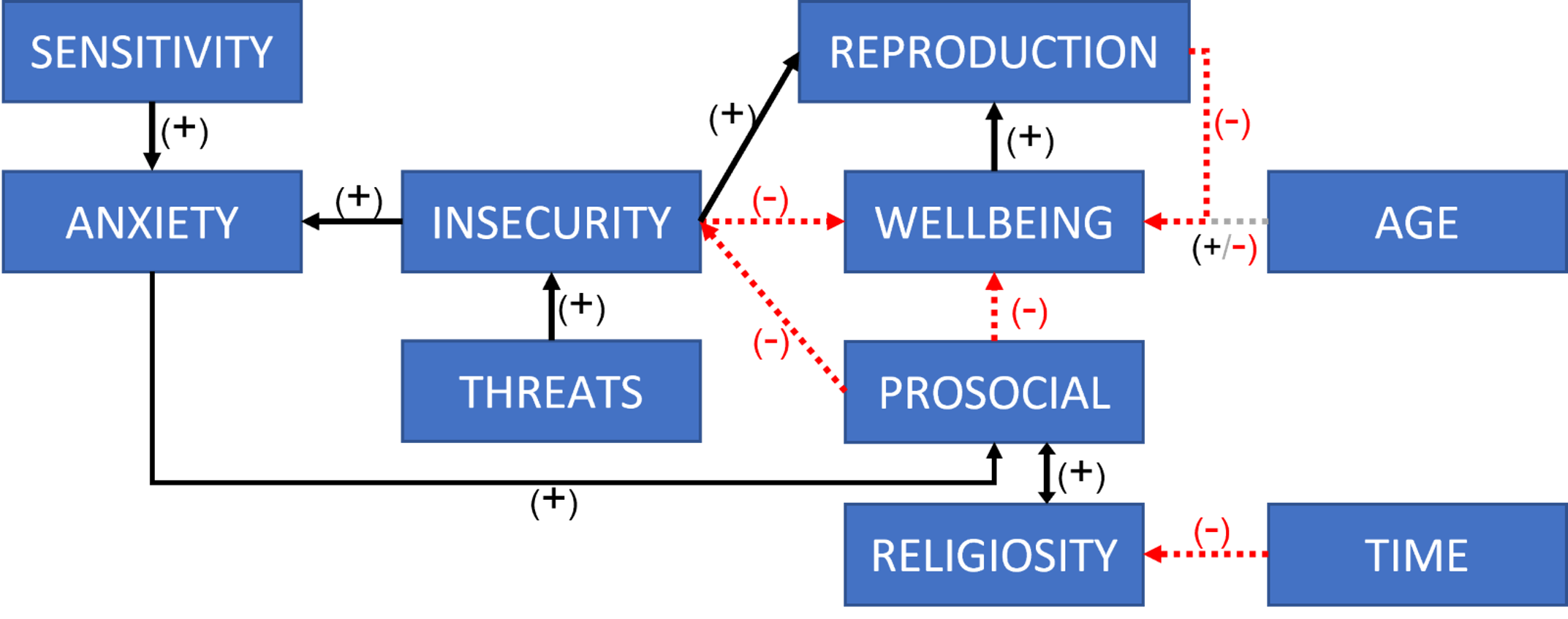
An agent-based model of prosocial equilibrium: Simulating the role of religiously motivated behaviour in the formation and maintenance of large-scale societies.
Authors: Puga-Gonzalez, L. Shults, R. Gore and K. Talmont-Kamisnki
This paper outlines a new agent-based model that represents the dynamics by which a society achieves and maintains prosocial equilibrium. The latter is understood as a social balance involving the interplay of prosocial behavior, anxiety, environmental threats, and religiosity in the population. Experiments showed that the model was able to simulate the emergence of relatively large societies under the sorts of conditions that would be expected based on the theoretical literature and other empirical findings in the relevant fields. We conclude by describing the main insights of the simulation experiments and pointing toward future work currently being planned by the research team.

Citizens initiatives in humanitarian aid: Lesvos, Greece as a case in bottom-up humanitarian assistance mobilization.
Authors: Frydenlund, E., Haaland, H., Padilla, J., and Wallevik H. (2023).
Through a focus on various CIGS (Citizens Initiatives for Global Solidarity) activities in Lesvos (Greece), this chapter characterizes the actions of civil societies during a situation of prolonged humanitarian assistance. Building on different types of empirical data (e.g. interviews, observations, web page analysis) collected on the island of Lesvos between 2016 and 2019, the chapter captures the evolution of CIGS in a humanitarian situation into phases that were motivated by changes in refugees and migrants’ needs.
Published in The Rise of Small-Scale Development Organisations: The Emergence, Positioning and Role of Citizen Aid Actors. 170-183. Routledge.
Murder on the VR Express: Studying the Impact of Thought Experiments at a Distance in Virtual Reality
Authors: Puga-Gonzalez, L. Shults, R. Gore and K. Talmont-Kamisnki
Hypothetical thought experiments allow researchers to gain insights into widespread moral intuitions and provide opportunities for individuals to explore their moral commitments. Previous thought experiment studies in virtual reality (VR) required participants to come to an on-site laboratory, which possibly restricted the study population, introduced an observer effect, and made internal reflection on the participants’ part more difficult. These shortcomings are particularly crucial today, as results from such studies are increasingly impacting the development of artificial intelligence systems, self-driving cars, and other technologies. This paper explores the viability of deploying thought experiments in commercially available in-home VR headsets. We conducted a study that presented the trolley problem, a life-and-death moral dilemma, through SideQuestVR, a third-party website and community that facilitates loading applications onto Oculus headsets. Thirty-three individuals were presented with one of two dilemmas: (1) a decision to save five lives at the cost of one life by pulling a switch and (2) a decision to save five lives at the cost of one life by pushing a person onto train tracks. The results were consistent with those of previous VR studies, suggesting that a “VR-at-a-distance” approach to thought experiments has a promising future while indicating lessons for future research.


Acceptance sampling to aid in the verification of computational simulations
Collins, A. J., Frydenlund, E., Lynch, C. J., and Robinson, R. M. (2022).
The paper proposes a systematic process in which a simulation inspector examines only a fraction of the computational model elements to measure the errors present. The proposed process could support established verification processes by sampling the simulation components to identify whether the model is acceptably error free and which components require correcting. The proposed methodology relies on several statistical constraints but serves the interests of simulation professionals as part of the overall verification process.
From Narratives to Conceptual Models via Natural Language Processing
Authors: Shuttleworth D., Padilla, J. (2022).
Conceptual modeling is considered a key step in the modeling and simulation process. Yet, it is not broadly practiced as there are no common standards and it is labor intensive. The paper focuses on the development of conceptual models assisted by natural language processing (NLP). The use of NLP would have a two-fold benefit: accelerate the development of conceptual models and facilitate communication across domains.
Winter Simulation Conference (WSC), Singapore, 2022, pp. 2222-2233, doi: 10.1109/WSC57314.2022.10015274.


Assessing Media’s Representation of Frustration Towards Venezuelan Migrants in Colombia
Authors: Llinas, B. Huseynli, G., Frydenlund, E., Palacio, K., Llinas, H., and Padilla, J. (2023).
This research utilizes statistical path modeling to examine the relationship between the number of Venezuelans migrating to Colombia and the media's coverage. The paper focuses on media coverage expressing frustration regarding migration, infrastructure, government, and geo-politics. Results suggest negative coverage indirectly contributes to increased coverage of infrastructure frustration.
SBP-BRiMS 2023. Pittsburgh, PA.
Extracting Information from Twitter Screenshots
Authors: T Zaki, ML Nelson, MC Weigle (2023)
Screenshots are prevalent on social media as a common approach for information sharing. Users rarely verify before sharing a screenshot whether the post it contains is fake or real. Information sharing through fake screenshots can be highly responsible for misinformation and disinformation spread on social media. Our ultimate goal is to develop a tool that could take a screenshot of a tweet and provide a probability that the tweet is real, using resources found on the live web and in web archives. This paper provides methods for extracting the tweet text, timestamp, and Twitter handle from a screenshot of a tweet.
arXiv preprint arXiv:2306.08236 2023


Hashes are not suitable to verify fixity of the public archived web
Authors: M Aturban, M Klein, H Van de Sompel, S Alam, ML Nelson, MC Weigle (2023)
Web archives, such as the Internet Archive, preserve the web and allow access to prior states of web pages. We implicitly trust their versions of archived pages, but as their role moves from preserving curios of the past to facilitating present day adjudication, we are concerned with verifying the fixity of archived web pages, or mementos, to ensure they have always remained unaltered. A widely used technique in digital preservation to verify the fixity of an archived resource is to periodically compute a cryptographic hash value on a resource and then compare it with a previous hash value. If the hash values generated on the same resource are identical, then the fixity of the resource is verified. We tested this process by conducting a study on 16,627 mementos from 17 public web archives. We replayed and downloaded the mementos 39 times using a headless browser over a period of 442 days and generated a hash for each memento after each download, resulting in 39 hashes per memento. The hash is calculated by including not only the content of the base HTML of a memento but also all embedded resources, such as images and style sheets. We expected to always observe the same hash for a memento regardless of the number of downloads. However, our results indicate that 88.45% of mementos produce more than one unique hash value, and about 16% (or one in six) of those mementos always produce different hash values.
PloS one 18 (6), e0286879 2023
PROJECTS

ODIN-EL
PI: Dr. Katie Smith, Co-PIs: Dr. Jessica Johnson, Dr. Deri Draper
Operationally Directed Instructional Network-Engineering Library (ODIN-EL) supports Commander, Navy Regional Maintenance Center and the Navy Afloat Maintenance Training Strategy (NAMTS) by collecting competency-based data and performing intelligent analytics on experiential knowledge transfer from master to apprentice maintainers. ODIN-EL provides actionable metrics and insights for the NAMTS program which tracks thousands of Sailors throughout their maintenance careers. These metrics inform on enrollment, participation, testing, and readiness across ashore and afloat program components. ODIN-EL strives to leverage the wealth of legacy training data and material of NAMTS while using an AI/ML enabled, competency-informed system to provide insights to program decision makers and tailor content recommendations to learners. All ODIN-EL components are delivered in collaboration with Valkyrie as a fully secure web application behind CAC authentication.
Hampton Roads GOTEC Program Pilot
As a founding member of the VA Maritime Industrial Base Consortium, MIBE launched the GO TEC pilot program in select Newport News, Hampton, Norfolk, and Portsmouth middle schools providing early exposure to target skills in coding, robotics, computer-assisted machining, and welding.

Coastal Coders: Adventures in Computational Thinking
Targeting a future workforce, Coastal Coders seeks to inform learners through immersive serious games and simulations connections between computer science and over nine emergent technologies revolutionizing sectors of the maritime industry. Users will explore computational thinking challenges and VDOE computer science standards as they navigate various careers and examples of maritime emergent technologies in their everyday lives. Dr. Jessica Johnson, Dr. Katie Smith, John Shull, BaTo Cvijetic, ODU Game Design students, and educators have worked to help design models, content, and themes throughout the project. Coastal Coders launches in Spring/Summer 2024 with expansion plans for regional school divisions and future funding across the state of Virginia, in addition to other research endeavors in the near future. This project is supported by funding via Newport News Public Schools and Newport News Shipbuilding.
Facilitating Self-Directedness: A Meta-Analysis Examining Learning Autonomy in Serious games
Dr. Jessica Johnson
The purpose of this study was to understand processes of learner autonomy that impact overall learning outcomes in serious simulations and serious games, synthesizing earlier empirical studies through a meta-analysis. The psychological requisite of learner autonomy is a central characteristic of serious games often elicited within situatedness of learning, transfer of learning, scaffolding, content and feedback, dynamic assessment, information design, and interactions of game design features. The study aimed to systematically synthesize research findings on degrees of learner autonomy as game mechanic and learning mechanic features that contribute to overall learning outcomes, in addition to ascertaining a taxonomy for future serious simulation development and studies in autonomous learning as a methodology of learning engineering.
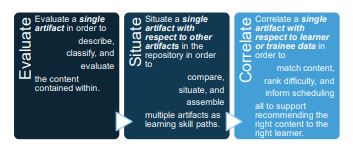
CACHE
PI: Dr. Katie Smith, CoPI: Dr.Jessica Johnson
Contribute, Approve, Curate, Hyper-Distribution Engine (CACHE), funded through a Phase II STTR from the Office of Naval Research, looks to use AI and machine learning to automate peer-to-peer knowledge sharing. CACHE is web-based knowledge curation and distribution system designed to make accessing content intuitive, efficient, and effective. Our team’s key role in this effort is to provide artificial intelligence/machine learning algorithms to curate, distribute and recommend content.
Machine-Learning Enabled Dependency Network Analysis for Quantifying Risks and Ripple Effects throughout the Supply Chain
PI: Dr. Rafael Diaz, Co-PI: Dr. Katie Smith
To overcome current limitations, we propose the development of a cybersecurity supply network Artificial Intelligence (AI) framework that enables characterizing shipbuilding supply networks and determining ripple effects from disruptions caused by cyberattacks to the supply network. By representing and replicating the collective behavior of relevant shipbuilding supply network nodes, shipbuilders can monitor and measure the effects of cybersecurity disruptions and test the reconfiguration options that minimize the detrimental effects on the supply network. It also enables the study of individual and simultaneous failure of one or more nodes and propagation effects across the network as a whole. This framework extends our previous novel risk management framework that considers complex tiered networks and systemic hypervulnerabilities (COVA CCI - 2021ODU-06.005).


Awards Ceremony Honors Eight Hampton Roads Graduates of the Work-Integrated Learning (WIL) Program
Dr. Mia Joe
Eight participants graduated from the Work-Integrated Learning (WIL) Program on Friday, August 18, 2023. A reception and award ceremony were held at the Holiday Inn in Newport News where each WIL participant received a plaque and certificate with a stipend they earned during the program. The Work-Integrated Learning Program is a gun violence prevention and intervention program funded from a grant from the Virginia Department of Criminal Justice. The program merges work-integrated learning with entrepreneurism through guided mentorship to decrease community gun violence and improve relationships with community systems to include the Newport News Police Department, local agencies, and community partners. The program was free to participants, aged 13-24, and were provided one-on-one and group mentoring, were taught how to start a business, and job readiness skills.
VMASC Year-In-Review FY 2023 Publications and Projects
As Virginia's premier university research center, the Old Dominion University (ODU) Virginia Modeling Analysis, and Simulation Center (VMASC) focuses on applied research leading to digital transformation. This Year-in-Review offers a retrospective glimpse into the 2023 Fiscal Year, highlighting a selection of the publications and projects our team members have been involved with over the year.
Multi-Level Impacts of Extreme Climate-Related Events on Food Supply Chain: Idaho Potato's Case Study
Authors: Liang Rahman, Md Mamunur, Nguyen, Ruby Thuy, Ezell, Barry, Charles, Boire, Liam D, and Hruska, Ryan C (2022)
Increased frequency and severity of climate related events threaten food security. While impacts on growers are well-studied, less is known about other stakeholders in the food supply chain (SC). This study aims to quantify the impacts of different extreme climate events on different stages of a potato SC. Agent-Based Modeling (ABM) was used to build a digital twin of the SC. Two experiments were conducted: (1) Severe drought, 50% of required water for irrigation is available. The contract price between farmers and processors increases by 20%. (2) Extreme weather, early frost or snow. The affected farmers lose 30% of the harvest. The speed of the delivery vehicles reduces by half. Results: The impacts of the disruption events were different on different agents in the supply chain for different product categories. The price hike of fresh potatoes was way higher than processed potatoes during disruptions. Non-contracted farmers gain additional revenues from the disruptions whereas contracted farmers incur a loss due to lock-in price and lower than usual harvest. The bad weather event caused 31% to 64% higher delivery lead times, while there was no impact from drought.
Reprioritizing Emergency Management Resources for Pandemic and Other Hazards
Authors: Ronnie E. Hill Jr., Davis C. Loose, DeAndre Johnson, Stacy McKinley, Wie Yusuf, Leigh M. Chapman, Thomas L. Polmateer, Barry C. Ezell, and James H. Lambert (2023)
Hazard mitigation planning, whether on a global, national, regional, or local level requires a multitude of organizations to collaborate on scenarios of mutual concern. Agencies strategize, develop, and implement plans for mitigating effects from manufactured and natural disasters. To develop more effective mitigation strategies, a typical agency uses a hazard gap analysis to identify gaps and evaluate the maturity of mitigation action strategies across jurisdictions. Issues of shared governance and competing perspectives create challenges for managing disasters across multiple tiers of government. This paper contributes a method to identify the agency perspectives on disaster risk that most matter to the allocations and priorities for shared resources. Each agency perspective is represented as a scenario of one or more emergent and future conditions. The conditions include health, environment, technologies, wear and tear, workforce, information, communication, obsolescence, regulation etc. In quantifying the disruption of system order, the paper presents an example of a risk register with 40 capabilities, six ordering criteria and eight scenarios. The new method coordinates data, evidence, experience, and imagination that are essential to systems analysis and negotiation of requirements among emergency managers in the post-pandemic era.
Published in the ASCE Journal for Natural Hazard.
The use of artificial intelligence to detect students' sentiments and emotions in gross anatomy reflections.
Authors: Rechowicz, K. J. & Elzie, C. A. (2023).
Students' reflective writings in gross anatomy provide a rich source of complex emotions experienced by learners. However, qualitative approaches to evaluating student writings are resource heavy and timely. To overcome this, natural language processing, a nascent field of artificial intelligence that uses computational techniques for the analysis and synthesis of text, was used to compare health professional students' reflections on the importance of various regions of the body to their own lives and those of the anatomical donor dissected. A total of 1365 anonymous writings (677 about a donor, 688 about self) were collected from 132 students. Binary and trinary sentiment analysis was performed, as well as emotion detection using the National Research Council Emotion Lexicon which classified text into eight emotions: anger, fear, sadness, disgust, surprise, anticipation, trust, and joy.
The most commonly written about body regions were the hands, heart, and brain. The reflections had an overwhelming positive sentiment with major contributing words “love” and “loved.” Predominant words such as “pain” contributed to the negative sentiments and reflected various ailments experienced by students and revealed through dissections of the donors. The top three emotions were trust, joy, and anticipation. Each body region evoked a unique combination of emotions. Similarities between student self-reflections and reflections about their donor were evident, suggesting a shared view of humanization and person-centeredness. Given the pervasiveness of reflections in anatomy, adopting a natural language processing approach to analysis could provide a rich source of new information related to students' previously undiscovered experiences and competencies.
From Cyclones to Cybersecurity: A Call for Convergence in Risk and Crisis Communications Research, PNAS Nexus (Submitted July 2023)
Authors: Ann Marie Reinhold, Ross J. Gore, Barry C. Ezell, Clemente Izurieta, and Elizabeth A.Shanahan, (2023)
A robust body of literature investigates mechanisms for improving risk communication because effective risk communication saves lives. While effective risk communication strategies are equally desired across different hazard domains (e.g., natural hazards, cyber security), the extent to which risk communication experts utilize the “lessons learned” from disciplines outside their own is suspect. Therefore, we hypothesized that risk communication research is siloed according to scientific disciplines at the detriment to the advancement of the field of risk communications research writ large. We test this hypothesis by evaluating the disciplinarity of 5,264 published papers using a combination of simple descriptive statistics, natural language processing, and hierarchical clustering. Finding that the risk communication research is siloed according to disciplinary lexicons, we present our findings as a call for convergence amongst our risk and crisis communication scholars to bridge across our disciplinary silos. In so doing, we will increase our ability to affect transformative change in the efficacy of our risk and crises messages.

Opportunities and Challenges of Using Computer-Based Simulation in Migration and Displacement Research: A Focus on Lesbos, Greece.
Authors: Frydenlund, E., and Padilla, J. (2022).
While simulation models have been used in the study of human migration, it is not broadly accepted as a research method. The chapter introduces the benefits and shortcomings of using simulation models to study migration and displacement.
Did They Really Tweet That? Querying Fact-Checking Sites and Politwoops to Determine Tweet Misattribution
Authors: C Bradford, ML Nelson (2022).
Screenshots of social media posts have become common place on social media sites. While screenshots definitely serve a purpose, their ubiquity enables the spread of fabricated screenshots of posts that were never actually made, thereby proliferating misattribution disinformation. With the motivation of detecting this type of disinformation, we researched developing methods of querying the Web for evidence of a tweet's existence. We developed software that automatically makes search queries utilizing the body of alleged tweets to a variety of services in an effort to find fact-check articles and other evidence of supposedly made tweets. We also developed tools to automatically search the site Politwoops for a particular tweet that may have been made and deleted by an elected official. In addition, we developed software to scrape fact-check articles from the sites Reuters.com and Snopes.com in order to derive a “truth rating" from any given article from these sites.


Robots still outnumber humans in web archives, but less than before
Authors: HR Jayanetti, K Garg, S Alam, ML Nelson, MC Weigle (2022).
To identify robots and humans and analyze their respective access patterns, we used the Internet Archive’s (IA) Wayback Machine access logs from 2012 and 2019, as well as Arquivo.pt’s (Portuguese Web Archive) access logs from 2019. We identified user sessions in the access logs and classified those sessions as human or robot based on their browsing behavior. To better understand how users navigate through the web archives, we evaluated these sessions to discover user access patterns. Based on the two archives and between the two years of IA access logs (2012 vs. 2019), we present a comparison of detected robots vs. humans and their user access patterns and temporal preferences. The total number of robots detected in IA 2012 is greater than in IA 2019 (21% more in requests and 18% more in sessions). Robots account for 98% of requests (97% of sessions) in Arquivo.pt (2019).
Securing Age-of-Information (AoI)-Enabled 5G Smart Warehouse Using Access Control Scheme
Authors: A. K. Das, S. Roy, E. Bandara and S. Shetty (2023).
Warehouses are becoming more dependent on connected technologies to support the tracking of items to the automated systems that may control these items (move to proper locations) or even support a manufacturing process. Wi-Fi is good but tends to struggle in large areas. We could overexpose a warehouse with many Wi-Fi access points, but this would increase the time to communicate (imagine a message having to jump to each access point to get from one end of the warehouse to the other). Instead, researchers are investigating the use of 5G wireless technology like what you would use on your smartphone but privately run just for the warehouse. In this type of system, the communication could occur faster as it would not have to jump through each access point due to the ability to manipulate the RF signal with powerful radios that can be dynamically reconfigured based on the needs and changing state of the warehouse.
To support this research endeavor, the researchers at CSICS/VMASC are contributing to ensure that the new system can operate fast, efficiently and most importantly secure! Many of the 5G sensors are very small with limited resources resulting in a low power requirement. New protocols are needed to maintain great security without the requirement of unlimited power and without compromising the benefits 5G brings to the speed of communication. In the paper titled "Securing Age-of-Information (AoI)-Enabled 5G Smart Warehouse Using Access Control Scheme", published in IEEE Internet of Things Journal this year, aims to design an energy-efficient certificate-based access control protocol, that will ensure the real-time and secure message communication among various participating agents of the smart warehouse. The authors describe the protocol encouraging other researchers to utilize and build on it, while additionally presenting performance results of test systems using the proposed protocol.


Quantum Resistance Cryptographic Methods to Improve Security in Health Medical Devices
Authors: P. Bagchi, B. Bera, A. K. Das, S. Shetty, P. Vijayakumar and M. Karuppiah
Cryptography, in particular public private key (PKI) cryptography is used to secure our communications over public networks. The security of PKI is measured by the time it would take classical computers to try different calculation of prime factors and identify the Key to decrypt the message data. Classical computers being binary in nature take a long time to do this type of calculation when the factors are very large which is the standard for PKI methods. Quantum computers (which are only implemented on a very small scale and performance today) are not binary in nature and allow for them to compute many more states at the same time compared to classical computers. Because of this, quantum computing could very easily identify the key to decode current cryptography best practices. Although it appears we are likely a couple of decades before quantum computers can crack current standards, researchers are currently planning and developing new cryptographic algorithms that can be “quantum resistant” where even if quantum computers would not be able to easily find the key in order to decrypt messages.
To support the research endeavor VMASC is partnering with International Institute of Information Technology, India to better utilize these new algorithms within known high level secure use cases. One of these use cases is in regard to personal private information related to medical healthcare devices. The team published the paper “Post Quantum Lattice-Based Secure Framework using Aggregate Signature for Ambient Intelligence Assisted Blockchain-Based IoT Applications” in IEEE Internet of Things Magazine this past March 2023. The paper describes how prior defined Lattice-Based public private key algorithms which would be hard for quantum computers to crack could be implemented within Internet of Things medical devices. The exchange of public keys and signatures were demonstrated using private blockchains with the idea of adding trust and transparency to the storage and update of key information. This algorithm ultimately provides an avenue for system implementors when quantum computers become more of a reality and is another instance of security researchers getting ahead of the attackers even when the attackers require new technology that is still being developed.
Estimating the health effects of adding bicycle and pedestrian paths at the census tract level: multiple model comparison
Authors: R. Gore, C. J. Lynch, C. A. Jordan, A. Collins, R. M. Robinson, G. Fuller, P. Ames, P. Keerthi, and Y. Kandukuri (2022)
Adding additional bicycle and pedestrian paths to an area can lead to improved health outcomes for residents over time. However, quantitatively determining which areas benefit more from bicycle and pedestrian paths, how many miles of bicycle and pedestrian paths are needed, and the health outcomes that may be most improved remain open questions. Our work provides and evaluates a methodology that offers actionable insight for city-level planners, public health officials, and decision makers tasked with the question “To what extent will adding specified bicycle and pedestrian path mileage to a census tract improve residents’ health outcomes over time?” We conducted a factor analysis of data from the American Community Survey, Center for Disease Control 500 Cities project, Strava, and bicycle and pedestrian path location and use data from two different cities (Norfolk, Virginia, and San Francisco, California).
We constructed 2 city-specific factor models and used an algorithm to predict the expected mean improvement that a specified number of bicycle and pedestrian path miles contributes to the identified health outcomes. We show that given a factor model constructed from data from 2011 to 2015, the number of additional bicycle and pedestrian path miles in 2016, and a specific census tract, our models forecast health outcome improvements in 2020 more accurately than 2 alternative approaches for both Norfolk, Virginia, and San Francisco, California. Furthermore, for each city, we show that the additional accuracy is a statistically significant improvement (P<.001 in every case) when compared with the alternate approaches. For Norfolk, Virginia (n=31 census tracts), our approach estimated, on average, the percentage of individuals with high blood pressure in the census tract within 1.49% (SD 0.85%), the percentage of individuals with diabetes in the census tract within 1.63% (SD 0.59%), and the percentage of individuals who had >2 weeks of poor physical health days in the census tract within 1.83% (SD 0.57%). For San Francisco (n=49 census tracts), our approach estimates, on average, that the percentage of individuals who had a stroke in the census tract is within 1.81% (SD 0.52%), and the percentage of individuals with diabetes in the census tract is within 1.26% (SD 0.91%).

Classifying Mathematics Teacher Questions to Support Mathematical Discourse.
Authors: Datta, Debaiyoti, Bywater, James P., Phillips, Maria, Lilly, Sarah, Chiu, Jennifer L., Watson, Ginger S., & Brown, Don E.
This paper examines whether natural language processing technologies can provide teachers with high-quality formative feedback about questioning practices that promote rich inclusive mathematical discourse within classrooms. This paper describes how a training dataset was collected and labeled using teacher questioning classifications that are grounded in the mathematics education literature, and it compares the performance of four classifier models fine-tuned using that dataset. Of the models tested, we find that RoBERTa, an open-source LLM, had a 76% accuracy in classifying questions. These modern transfer-learning based approaches require significantly fewer data points than traditional machine-learning methods and are ideal in low-resource scenarios like question classification. The paper concludes by discussing potential use cases within the field of mathematics teacher education and describes how the classifier models created can be publicly accessed.
An agent-based model of prosocial equilibrium: Simulating the role of religiously motivated behaviour in the formation and maintenance of large-scale societies.
Authors: Puga-Gonzalez, L. Shults, R. Gore and K. Talmont-Kamisnki
This paper outlines a new agent-based model that represents the dynamics by which a society achieves and maintains prosocial equilibrium. The latter is understood as a social balance involving the interplay of prosocial behavior, anxiety, environmental threats, and religiosity in the population. Experiments showed that the model was able to simulate the emergence of relatively large societies under the sorts of conditions that would be expected based on the theoretical literature and other empirical findings in the relevant fields. We conclude by describing the main insights of the simulation experiments and pointing toward future work currently being planned by the research team.


Citizens initiatives in humanitarian aid: Lesvos, Greece as a case in bottom-up humanitarian assistance mobilization.
Authors: Frydenlund, E., Haaland, H., Padilla, J., and Wallevik H. (2023).
Through a focus on various CIGS (Citizens Initiatives for Global Solidarity) activities in Lesvos (Greece), this chapter characterizes the actions of civil societies during a situation of prolonged humanitarian assistance. Building on different types of empirical data (e.g. interviews, observations, web page analysis) collected on the island of Lesvos between 2016 and 2019, the chapter captures the evolution of CIGS in a humanitarian situation into phases that were motivated by changes in refugees and migrants’ needs.
Published in The Rise of Small-Scale Development Organisations: The Emergence, Positioning and Role of Citizen Aid Actors. 170-183. Routledge.
Murder on the VR Express: Studying the Impact of Thought Experiments at a Distance in Virtual Reality
Authors: Puga-Gonzalez, L. Shults, R. Gore and K. Talmont-Kamisnki
Hypothetical thought experiments allow researchers to gain insights into widespread moral intuitions and provide opportunities for individuals to explore their moral commitments. Previous thought experiment studies in virtual reality (VR) required participants to come to an on-site laboratory, which possibly restricted the study population, introduced an observer effect, and made internal reflection on the participants’ part more difficult. These shortcomings are particularly crucial today, as results from such studies are increasingly impacting the development of artificial intelligence systems, self-driving cars, and other technologies. This paper explores the viability of deploying thought experiments in commercially available in-home VR headsets. We conducted a study that presented the trolley problem, a life-and-death moral dilemma, through SideQuestVR, a third-party website and community that facilitates loading applications onto Oculus headsets. Thirty-three individuals were presented with one of two dilemmas: (1) a decision to save five lives at the cost of one life by pulling a switch and (2) a decision to save five lives at the cost of one life by pushing a person onto train tracks. The results were consistent with those of previous VR studies, suggesting that a “VR-at-a-distance” approach to thought experiments has a promising future while indicating lessons for future research.


Acceptance sampling to aid in the verification of computational simulations
Collins, A. J., Frydenlund, E., Lynch, C. J., and Robinson, R. M. (2022).
The paper proposes a systematic process in which a simulation inspector examines only a fraction of the computational model elements to measure the errors present. The proposed process could support established verification processes by sampling the simulation components to identify whether the model is acceptably error free and which components require correcting. The proposed methodology relies on several statistical constraints but serves the interests of simulation professionals as part of the overall verification process.
From Narratives to Conceptual Models via Natural Language Processing
Authors: Shuttleworth D., Padilla, J. (2022).
Conceptual modeling is considered a key step in the modeling and simulation process. Yet, it is not broadly practiced as there are no common standards and it is labor intensive. The paper focuses on the development of conceptual models assisted by natural language processing (NLP). The use of NLP would have a two-fold benefit: accelerate the development of conceptual models and facilitate communication across domains.
Winter Simulation Conference (WSC), Singapore, 2022, pp. 2222-2233, doi: 10.1109/WSC57314.2022.10015274.


Assessing Media’s Representation of Frustration Towards Venezuelan Migrants in Colombia
Authors: Llinas, B. Huseynli, G., Frydenlund, E., Palacio, K., Llinas, H., and Padilla, J. (2023).
This research utilizes statistical path modeling to examine the relationship between the number of Venezuelans migrating to Colombia and the media's coverage. The paper focuses on media coverage expressing frustration regarding migration, infrastructure, government, and geo-politics. Results suggest negative coverage indirectly contributes to increased coverage of infrastructure frustration.
SBP-BRiMS 2023. Pittsburgh, PA.
Extracting Information from Twitter Screenshots
Authors: T Zaki, ML Nelson, MC Weigle (2023)
Screenshots are prevalent on social media as a common approach for information sharing. Users rarely verify before sharing a screenshot whether the post it contains is fake or real. Information sharing through fake screenshots can be highly responsible for misinformation and disinformation spread on social media. Our ultimate goal is to develop a tool that could take a screenshot of a tweet and provide a probability that the tweet is real, using resources found on the live web and in web archives. This paper provides methods for extracting the tweet text, timestamp, and Twitter handle from a screenshot of a tweet.
arXiv preprint arXiv:2306.08236 2023

Hashes are not suitable to verify fixity of the public archived web
Authors: M Aturban, M Klein, H Van de Sompel, S Alam, ML Nelson, MC Weigle (2023)
Web archives, such as the Internet Archive, preserve the web and allow access to prior states of web pages. We implicitly trust their versions of archived pages, but as their role moves from preserving curios of the past to facilitating present day adjudication, we are concerned with verifying the fixity of archived web pages, or mementos, to ensure they have always remained unaltered. A widely used technique in digital preservation to verify the fixity of an archived resource is to periodically compute a cryptographic hash value on a resource and then compare it with a previous hash value. If the hash values generated on the same resource are identical, then the fixity of the resource is verified. We tested this process by conducting a study on 16,627 mementos from 17 public web archives. We replayed and downloaded the mementos 39 times using a headless browser over a period of 442 days and generated a hash for each memento after each download, resulting in 39 hashes per memento. The hash is calculated by including not only the content of the base HTML of a memento but also all embedded resources, such as images and style sheets. We expected to always observe the same hash for a memento regardless of the number of downloads. However, our results indicate that 88.45% of mementos produce more than one unique hash value, and about 16% (or one in six) of those mementos always produce different hash values.
PloS one 18 (6), e0286879 2023
PROJECTS

ODIN-EL
PI: Dr. Katie Smith, Co-PIs: Dr. Jessica Johnson, Dr. Deri Draper
Operationally Directed Instructional Network-Engineering Library (ODIN-EL) supports Commander, Navy Regional Maintenance Center and the Navy Afloat Maintenance Training Strategy (NAMTS) by collecting competency-based data and performing intelligent analytics on experiential knowledge transfer from master to apprentice maintainers. ODIN-EL provides actionable metrics and insights for the NAMTS program which tracks thousands of Sailors throughout their maintenance careers. These metrics inform on enrollment, participation, testing, and readiness across ashore and afloat program components. ODIN-EL strives to leverage the wealth of legacy training data and material of NAMTS while using an AI/ML enabled, competency-informed system to provide insights to program decision makers and tailor content recommendations to learners. All ODIN-EL components are delivered in collaboration with Valkyrie as a fully secure web application behind CAC authentication.
Hampton Roads GOTEC Program Pilot
As a founding member of the VA Maritime Industrial Base Consortium, MIBE launched the GO TEC pilot program in select Newport News, Hampton, Norfolk, and Portsmouth middle schools providing early exposure to target skills in coding, robotics, computer-assisted machining, and welding.


Coastal Coders: Adventures in Computational Thinking
Targeting a future workforce, Coastal Coders seeks to inform learners through immersive serious games and simulations connections between computer science and over nine emergent technologies revolutionizing sectors of the maritime industry. Users will explore computational thinking challenges and VDOE computer science standards as they navigate various careers and examples of maritime emergent technologies in their everyday lives. Dr. Jessica Johnson, Dr. Katie Smith, John Shull, BaTo Cvijetic, ODU Game Design students, and educators have worked to help design models, content, and themes throughout the project. Coastal Coders launches in Spring/Summer 2024 with expansion plans for regional school divisions and future funding across the state of Virginia, in addition to other research endeavors in the near future. This project is supported by funding via Newport News Public Schools and Newport News Shipbuilding.
Facilitating Self-Directedness: A Meta-Analysis Examining Learning Autonomy in Serious games
Dr. Jessica Johnson
The purpose of this study was to understand processes of learner autonomy that impact overall learning outcomes in serious simulations and serious games, synthesizing earlier empirical studies through a meta-analysis. The psychological requisite of learner autonomy is a central characteristic of serious games often elicited within situatedness of learning, transfer of learning, scaffolding, content and feedback, dynamic assessment, information design, and interactions of game design features. The study aimed to systematically synthesize research findings on degrees of learner autonomy as game mechanic and learning mechanic features that contribute to overall learning outcomes, in addition to ascertaining a taxonomy for future serious simulation development and studies in autonomous learning as a methodology of learning engineering.


CACHE
PI: Dr. Katie Smith, CoPI: Dr.Jessica Johnson
Contribute, Approve, Curate, Hyper-Distribution Engine (CACHE), funded through a Phase II STTR from the Office of Naval Research, looks to use AI and machine learning to automate peer-to-peer knowledge sharing. CACHE is web-based knowledge curation and distribution system designed to make accessing content intuitive, efficient, and effective. Our team’s key role in this effort is to provide artificial intelligence/machine learning algorithms to curate, distribute and recommend content.
Machine-Learning Enabled Dependency Network Analysis for Quantifying Risks and Ripple Effects throughout the Supply Chain
PI: Dr. Rafael Diaz, Co-PI: Dr. Katie Smith
To overcome current limitations, we propose the development of a cybersecurity supply network Artificial Intelligence (AI) framework that enables characterizing shipbuilding supply networks and determining ripple effects from disruptions caused by cyberattacks to the supply network. By representing and replicating the collective behavior of relevant shipbuilding supply network nodes, shipbuilders can monitor and measure the effects of cybersecurity disruptions and test the reconfiguration options that minimize the detrimental effects on the supply network. It also enables the study of individual and simultaneous failure of one or more nodes and propagation effects across the network as a whole. This framework extends our previous novel risk management framework that considers complex tiered networks and systemic hypervulnerabilities (COVA CCI - 2021ODU-06.005).


Awards Ceremony Honors Eight Hampton Roads Graduates of the Work-Integrated Learning (WIL) Program
Dr. Mia Joe
Eight participants graduated from the Work-Integrated Learning (WIL) Program on Friday, August 18, 2023. A reception and award ceremony were held at the Holiday Inn in Newport News where each WIL participant received a plaque and certificate with a stipend they earned during the program. The Work-Integrated Learning Program is a gun violence prevention and intervention program funded from a grant from the Virginia Department of Criminal Justice. The program merges work-integrated learning with entrepreneurism through guided mentorship to decrease community gun violence and improve relationships with community systems to include the Newport News Police Department, local agencies, and community partners. The program was free to participants, aged 13-24, and were provided one-on-one and group mentoring, were taught how to start a business, and job readiness skills.



